Altening Malware Analysis
TLDR;
Don’t download the authenticator
Introduction
Alt-account websites offer Minecraft accounts for a fraction of the official cost. One of the most popular alt-account sales is called “The Altening”.
I was curious about how the website gets these accounts for pennies on the dollar so I starting looking at their website, and saw that it prompts users to run their “authenticator” to access free Minecraft accounts.
When I downloaded the authenticator it was a zip file with a single exe file. I think the exe is in the zip file partially because it makes it less likely to be flagged as possibly dangerous when it is being downloaded.
Out of curiosity I started to analyze the file to see what it could be doing other than its advertised function.
First Look
The first thing I did with the exe file was put it though virus total. Virus total is a free website that automatically runs the file though many antiviruses.
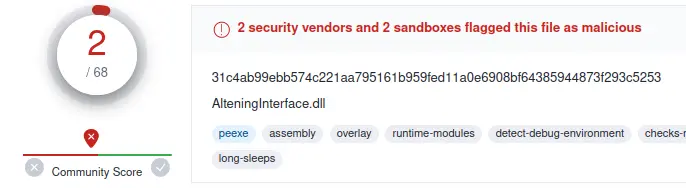
Virus total showed the two antiviruses that flagged the file: Gridnsoft, and Zillya. Grindnsoft thought that the file was Malware.Win64.RedLine.bot. That is a specific strain of information stealer malware. Exactly what I suspected the file to be.
Zillya detected the file as Trojan.Crypt.Win32.80263. That means that the antivirus suspects the file of trying to obfuscate its activity.
Static Analysis
I started with a static analysis of the file. Static analysis is seeing what is in the executable without running it. I used two tools to do this, Ghirda, and Binary Ninja.
Virus total suspected the file of obfuscating itself so I was not expecting to find anything through static analysis.
Ghirda
Ghirda is a free and open source static analysis program developed by the NSA. It is able to disassemble programs and write pseudo code with varying levels of abstraction.
When I looked through the output, there was not much of interest. I could not find anything blatantly malicious, but I have little experience with malware analysis, and maybe someone else with more knowledge could find something.
Binary Ninja
Binary ninja works similarly to Ghirda. It is proprietary, but it also has a nicer UI in my opinion.
I had roughly the same results as I did with Ghirda. I could not find anything blatantly malicious, but I am also not familiar with the tool so I could have very easily missed something.
Dynamic Analysis
After I could not understand fully what the program was doing with static analysis I decided to try some dynamic analysis. Dynamic analysis is when you run the program and see what it does. Some common tools for this are strace for linux, and WinDBG for windows.
When you use dynamic analysis you detonate the malware. Do not do this unless you have carefully setup a sandboxed environment.
This file is an windows EXE file, so I used WinDBG to analyze it.
Isolated Environment
I setup a virtual machine using QEMU/KVM with the virt-manager frontend. I already had a windows malware analysis virtual machine setup so I cloned that.
If you are planning on doing dynamic analysis I would recommend using a cloud virtual machine and remotely connecting to that so you don’t have to worry about VM breaking malware.
WinDBG
WinDBG records what an application does as it executes. Nothing from WinDBG was obviously malicious. It did not try to change files in bulk, but because this is likely an information grabber and not ransomeware that is not an expected behavior.
Here is a link to the dump if you are interested
Suspicious Permissions
Without even looking at the dumps there was some very apparent suspicious behavior in what permissions the file wanted. Firstly, it needed to be run as administrator to even start. This is not on its own very suspicious, but when you think about what it is doing it is odd.
Why would a program, with its supposed purpose of simply acting as a Minecraft launcher need administrator permissions to even launch.
Suspicious Certificates
The biggest red flag this program raised was wanting to act as the certificate authority for auth.mojang.com and sessionserver.mojang.com.
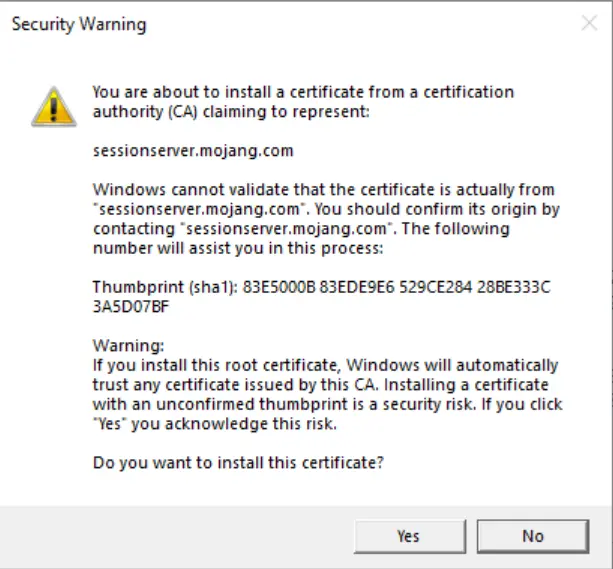
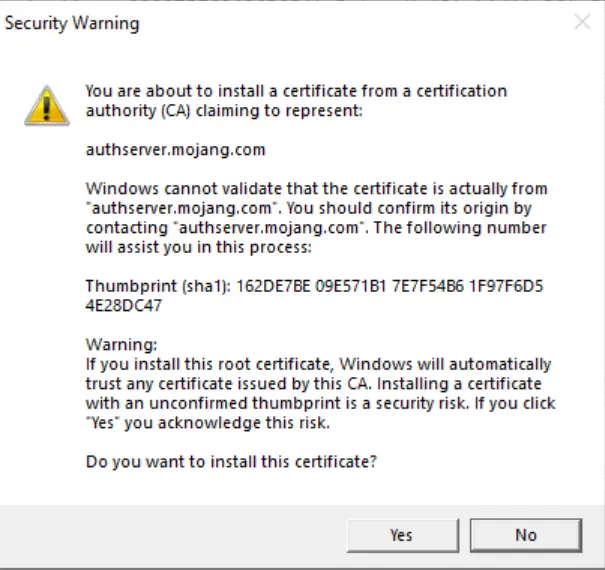
Allowing these certificates to be added to your computer makes you very vulnerable to man in the middle attacks. Man in the middle attacks are where an attacker stands in between you and the computer you are trying to connect to and reads the information passing through.
Under normal circumstances Certificate Authorities can protect you from these attacks because they provide an authoritative source on what public encryption keys are valid for that website.
When you press yes on these boxes you are allowing The Altening to change what public encrpytion keys are associated with the website. While simultaneously giving it the ability to sniff all network traffic on your computer because it was already run as administrator.
This is at worst malicious, and at best very bad design. Giving them the benefit of the doubt, in the best case there is a man in the middle attack when The Altening is replacing your login credentials with the login credentials for the alternate account.
Even in this best case scenario it is still very insecure. You are putting a massive amount of trust in the security of their certificate authority, and even more trust in them.
Conclusion
It is very likely that the Altening’s authenticator is malicious, and I could never recommend that anyone download it. In the best case scenario it puts a large amount of your accounts security in The Altening’s hands. In a more likely scenario your account is being stolen by them.
It is important to remember that they are somehow making money selling $29.99 accounts for as little as $1.49. They are getting their accounts from somewhere, and their suspicious software might have something to do with it.