Securing my Electronics for DEF CON
Intro - What is DEFCON
DEFCON is one of the largest cybersecurity conventions in the world. Every year it takes place in Vegas and brings people from all over. Having all of those hackers in one place makes for a fun environment with lots of learning opportunities, but it also makes an environment where your threat model has to be a little bit more extreme.

My Threat Model
The bottom line is I am not a particularly interesting person to hack. I am a 16 year old without a bank account to speak of. This however does not mean I will not secure my things.
The main attackers I am protecting against are people who want to hack into laptops and phones for the sake of doing it. This means I am likely spared from any new zero days that could be better spent on world leaders.
One of the main motivators for securing my electronics is fun. I am going a little bit further than I probably need to.
Attack Vectors
My three biggest concerns are
- Downloading malware (as always)
- Getting my electronics stolen
- Network/Wireless attacks
Downloading Malware
I think the general digital hygiene that I take in my day to day life is probably strong enough to protect against downloading malware. I only download signed packages from my package manager, and if I am downloading something that is not from my package manager I make an effort to read the source code.
I don’t think my risk of downloading malware goes up significantly at DEF CON because I don’t plan on downloading software at all.
Getting My Electronics Stolen
There is always a risk of getting electronics stolen, especially when you are traveling. This is not a DEF CON specific risk, but I think it is enough of a risk to be worth mentioning.
To mitigate the damage that could be caused by getting my electronics stolen I have both my laptop and phone full disk encrypted. I don’t think my laptop is likely to be stolen because it is an old Thinkpad that I found in the trash, but I will keep an extra close eye on my phone.
Full disk encryption should make it so that the only damage that would come from getting my laptop or phone stolen, is that I would no longer have a laptop or phone. I would not have to worry about any saved logins or other sensitive information.
Wireless/Network Attacks
I am writing about this more because it is fun to mitigate these attacks, than because they are a tremendous risk to me. They are much more of a risk for people with more aggressive threat models.
Wall of Sheep
I believe the highest wireless attack risk for me is ending up on the wall of sheep. The wall of sheep is a list of the usernames and passwords of people who were not using proper encryption when they logged into something on the insecure DEF CON network.
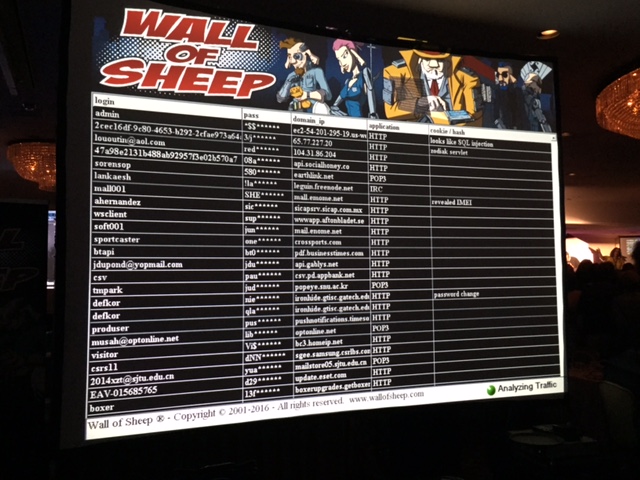
I plan on staying off the wall of sheep by only connecting to the internet though a tethered hotspot. This should eliminate the risk because the wall of sheep only includes people from the insecure DEF CON network.
Overall Wireless Safety
I am going to turn off WiFi and bluetooth on both my laptop and phone, and only communicate with the outside world over LTE.